ENTERPRISE SOLUTIONS
Enterprise solutions for big business.
SMALL BUSINESSES & ORGANIZATIONS
Small to Medium Businesses and Organizations.
INDIVIDUALS
Individuals or Small-Office/Home-Office Solutions.
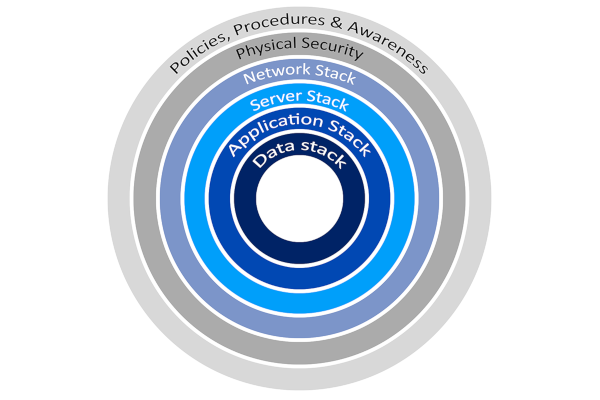
POLICY AND PROCEDURE DEVELOPMENT, COMPLIANCE, GAP ANALYSIS & USER TRAINING
Proper development of policies and procedures and training users in how to comply is key.
ENDPOINT (DESKTOP & SERVER) SECURITY
The majority of your valuable assets can be found at the endpoints of your network – your servers and desktop computers.
NETWORK SECURITY ANALYSIS & DEVELOPMENT
A complete analysis of devices and protocols on your network is the first step to securing it.
DATA PROTECTION
A variety of methods can be used to secure your data. One of the most important of these methods is regular backups.
PENETRATION TESTING
Penetration testing is the process of analyzing a computer network and devices to determine weaknesses and then taking steps to mitigate those weaknesses.
Installation
We can install and secure your complete infrastructure.
Got Your Six Cybersecurity have the skills needed to secure your resources. They can deploy both software and hardware based security objects. They can keep tabs on your systems so you continue to feel secure.
Got Your Six can do a complete end to end analysis of your organization and come up with a straightforward and effective plan to secure your environment. They can follow that up with excellent training.
Analysis and penetration testing performed by Got Your Six can reveal vulnerabilities that you were completely unaware of. They can patch those holes quickly and make you more secure.






Rob Wilson
Founder & Chief Technology Officer

Thom Robichaud
Founder & Director of Operations