Penetration testing is the process of analyzing a computer network and devices to determine weaknesses and then taking steps to mitigate those weaknesses.
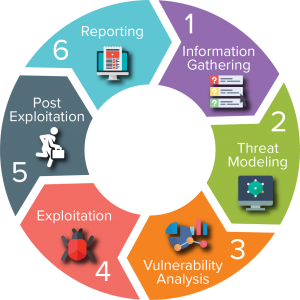 Penetration testing also called pen testing or ethical hacking is the practice of testing a computer system, network or web application to find security vulnerabilities that an attacker could exploit. Penetration testing can be automated with
Penetration testing also called pen testing or ethical hacking is the practice of testing a computer system, network or web application to find security vulnerabilities that an attacker could exploit. Penetration testing can be automated with
software applications or performed manually. Either way, the process involves gathering information about the target before the test, identifying possible entry points, attempting to break in — either virtually or for real — and reporting back the findings.
Typically, the information about security weaknesses that are identified or exploited through pen testing is aggregated and provided to the organization’s IT and network system managers, enabling them to make strategic decisions and prioritize remediation efforts.
Penetration tests are also sometimes called white hat attacks because, in a pen test, the good guys are attempting to break in.
Purpose of penetration testing
The primary goal of a pen test is to identify weak spots in an organization’s security posture, as well as measure the compliance of its security policy, test the staff’s awareness of security issues and determine whether — and how — the organization would be subject to security disasters.
A penetration test can also highlight weaknesses in a company’s security policies. For instance, although a security policy focuses on preventing and detecting an attack on an enterprise’s systems, that policy may not include a process to expel a hacker. Penetrating testing responsibilities vary for different mixes of cloud and on-premise systems.
The reports generated by a penetration test provide the feedback needed for an organization to prioritize the investments it plans to make in its security. These reports can also help application developers create more secure apps. If developers understand how hackers broke into the applications they helped develop, the intention is to motivate developers to enhance their education around security so they won’t make the same or similar errors in the future.
